CAC ON YOUR Mac INSTALL CHECKLIST PAGE for Mac OS 15.x Sequoia, 14.x Sonoma, and Mac 13.x Ventura |
||||||||||||||||||||||||||||||||||||||||||||||||||
|
NOTE: Mac OS Monterey and Ventura look more like iOS, which is why this special page was created
6 "high level" steps needed, follow down the page to make this a painless systematic process
Step 1: Is your CAC reader Mac friendly? Visit the USB Readers page or USB-C Readers page to verify the CAC reader you have is Mac friendly. "Some, not all" CAC readers may need to have a driver installed to make it work.
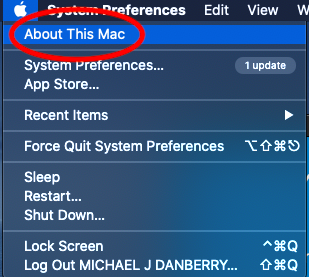
Step 2: Can your Mac "see" the reader? Plug the CAC reader into an open USB port before proceeding, give it a few moments to install Step 2a: Click the Apple Icon in the upper left corner of the desktop, select "About This Mac"
Step 2b: Click "More Info..." (button), (image is from an Intel based Mac, screen will look similar with an M processor)
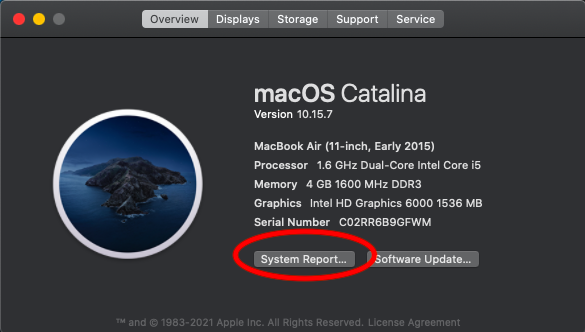
Select "General", then "System Report..."
Step 2c: Verify the CAC reader shows in Hardware, USB, under USB Device Tree. Different readers will show differently, most readers have no problem in this step.
Step 3: Verify which version of MacOS you have?
Step 3a: Click the Apple Icon in the upper left corner of your desktop and select "About This Mac"
Step 3b: Look next to macOS for: Example: Ventura 13.0.1 (image is from an Intel based Mac, screen will look similar with an M processor)
Step 4: Figure out which CAC (ID Card) you have
Look at the top back of your ID card for these card types. If you have any version other than the seven shown below, you need to visit an ID card office and have it replaced. All CACs [other than these six] were supposed to be replaced prior to 1 October 2012. A guide to help figure out which CAC you have
Find out how to flip card over video
Step 5: Install the DoD certificates (for Safari and Chrome Users)
Go to Keychain Access Click: Go (top of screen), Utilities, double click Keychain Access.app
(You can also type: keychain access using Spotlight (this is my preferred method))
Select login (under Default Keychains), and select All Items
Download each of the 4 files via links below (you may need to click Allow on each link) Save to your downloads folder
Please know... IF You have any DoD certificates already located in your keychain access, please delete them prior to running the AllCerts.p7b file below.
https://militarycac.com/maccerts/AllCerts.p7b, https://militarycac.com/maccerts/RootCert3.cer, https://militarycac.com/maccerts/RootCert4.cer, https://militarycac.com/maccerts/RootCert5.cer, and https://militarycac.com/maccerts/RootCert6.cer
Double click each of the files to install certificates into the login section of keychain
Select the Kind column, verify the arrow is pointing up, scroll down to certificate, look for all of the following certificates:
DOD DERILITY CA-1, DOD DERILITY CA-3 through CA-4 DOD EMAIL CA-59, DOD EMAIL CA-62 through DOD EMAIL CA-65, DOD EMAIL 70 through 73, DOD ID CA-59, DOD ID CA-62 through DOD ID CA-65, DOD ID CA-70 through 73, DoD Root CA 3 through DoD Root CA 6, DOD SW CA-60 through DOD SW CA-61, DOD SW CA-66 through DOD SW CA-69, and DOD SW CA-74 through 77
NOTE: If you are missing any of the above certificates, you have 2 choices, 1. Delete all of them, and re-run the 5 files above, or 2. Download the allcerts.zip file and install each of the certificates you are missing individually.
You may notice some of the certificates will have a red circle with a white X
You need to manually trust the DoD Root CA 3, 4, 5, & 6 certificates Double click each of the DoD Root CA certificates, select the triangle next to Trust, in the When using this certificate: select Always Trust, repeat until all 3 do not have the red circle with a white X.
You may be prompted to enter computer password when you close the window, afterwards it will now show as trusted
Once you select Always Trust, your icon will have a light blue circle with a white + on it.
The "bad certs" that have caused problems for Windows users may show up in the keychain access section on some Macs. These need to be deleted / moved to trash.
The DoD Root CA 2 & 3 you are removing has a light blue frame, leave the yellow frame DoD Root CA 3 version. The icons may or may not have a red circle with the white x
If you have tried accessing CAC enabled sites prior to following these instructions, please go through this page before proceeding Clearing the keychain (opens a new page) Please come back to this page to continue installation instructions.
Try to access the CAC enabled site you need to access now. . When you plug your reader in, you will see a message like this Click the little white X, if you Pair, you risk the chance of blocking your card:
Mac OS Ventura finally gives us the number of PIN tries remaining if you enter your PIN incorrectly
If you have problems, please follow images below to verify if your CAC is being read by your computer
Click the Apple Icon in the upper left corner of the desktop, select "About This Mac"
Click the "System Report..." button (image is from an Intel based Mac, screen will look similar with an M processor)
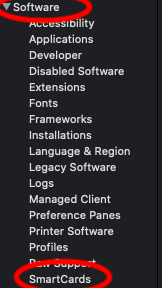
Scroll down the left column to the "Software" section then click on "SmartCards"
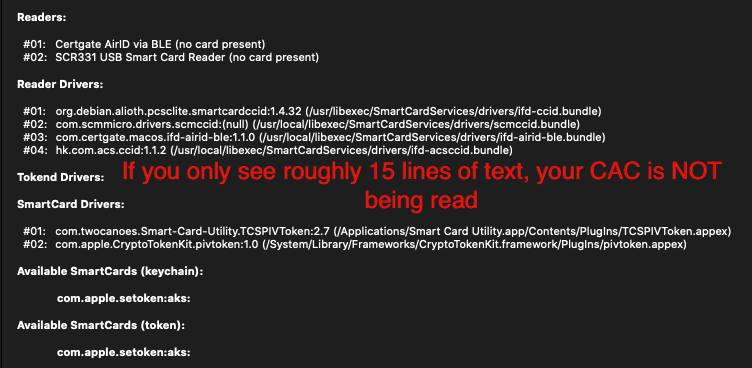
If you see hundreds of lines of "gibberish" these are your certificates being read from your CAC.
Example of CAC not being read. You'll only see roughly15 lines of text.
Idea #1 to try: Re-enable your native smart card support via instructions here: https://militarycac.com/macuninstall.htm#re-enable
Idea #2 to try: It could mean your CAC reader needs a driver or firmware update. Look for your reader on the CAC readers page to verify if your reader and CAC combination is compatible with each other.
Mac support provided by: Michael Danberry |
||||||||||||||||||||||||||||||||||||||||||||||||||
If you have questions or suggestions for this site, contact Michael J. Danberry
Last Update or Review: Tuesday, 01 October 2024 16:38 hrs
The following domain
names all resolve to the same website: ChiefsCACSite.com,
CommonAccessCard.us, CommonAccessCard.info, & ChiefGeek.us
|